Active Directory Integration with Dante Domain Manager
Connecting to an Active Directory Server
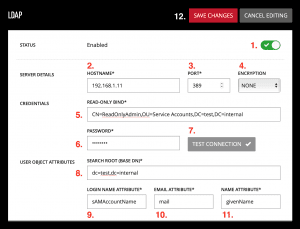
- Navigate to the Settings / External Services panel and toggle the slider in the LDAP section to enable LDAP.
- Enter the Hostname or IP address of your Active Directory server.
- Enter the port used to connect and authenticate with your Active Directory server. The default port for LDAP / StartTLS is 389, and the default port for LDAPS is 636.
- If your LDAP server is configured to use an encrypted connection, select the appropriate encryption protocol here to enable encrypted communication between DDM and the LDAP server (supported protocols are LDAPS and StartTLS).
- In the Credentials section enter the full bind string for the administrator user. (Note: The administrator account must have sufficient permissions to search the LDAP database for any user object and attributes you’ll need to access from this server. Write access is not required)
- The full Bind for your Administrator is usually the “distinguishedName” attribute value.
- Enter the password for the administrator user.
- Click the Test Connection button. If successful, the button will display a checkmark.
- In the Directory Entry Attributes section first enter the Search Root (Base DN) for the users you wish to add to the DDM user pool. This could be just your “DC” or could include the specific “OU” you want to search for users in.
- Enter the Login Name Attribute that users will use to login to the DDM Server and Dante Controller.
- Typically for Active Directory this is the “sAMAccountName” attribute.
- Enter the Email Attribute that DDM will use for email notifications.
- Typically for Active Directory this is the “mail” attribute.
- Enter the Name Attribute that the DDM will use for displayed names.
- Typically for Active Directory this is the “givenName” attribute.
- Click Save Changes.
LDAP Groups
The LDAP Groups panel is used to define groups of Active Directory users for the assignment of Dante Domain Manager privileges.
Note: Groups defined here are defined only on the DDM server. No changes are sent to the Active Directory server.
- Enter a Name for the group. This name does not have to relate to any group names in the Active Directory server.
- Enter an LDAP Query that returns the LDAP nodes belonging to users in the group.
- Click the Test Query button to list the users who match the current query.
- Select a Default Role for the group.
- Optional: add Domain Specific Privileges for the group.
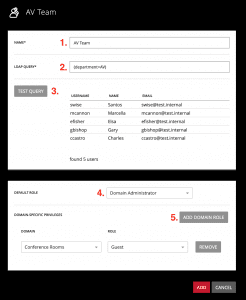
Note: A user can be a member of more than one group; their privileges add together between groups. Domain-specific privileges override default privileges for a particular group, but will not remove default permissions granted by a different group.
LDAP Query Examples
- Any attribute users have can be easily queried
- Example: If I want to query for all users in the “AV” department, I could use the LDAP query
- (department=AV)
- Example: I want to give a specific user Site Administrator rights:
- (sAMAccountName=aedwards)
- Example: If I want to query for all users in the “AV” department, I could use the LDAP query
- Multiple attributes can be combined in queries
- Example: If I only want to query members of the “AV” department that have the role (title) of “Engineer,” I could use the LDAP query
- (&(department=AV)(title=Engineer))
- Example: If I want to query all users that are not Managers, I could use the query:
- (&(objectClass=user)(!(title=Manager)))
- Example: If I only want to query members of the “AV” department that have the role (title) of “Engineer,” I could use the LDAP query
- MemberOf queries can be used but the syntax is a bit more verbose and must include the full bind for the group.
- Example: I want to query for all members of the “Network Admins” group.
- (MemberOf=CN=Network Admins,OU=Groups,DC=example,DC=com)
- Example: I want to query for all members of the “Network Admins” group.
Note: The results from “Test Query” might include entries that say Missing. In this case, the query is matching nodes that do not contain one or more of the user attributes configured in the External Services panel. Consider adding additional conditions to the query or narrowing down the Search Root (Base DN) with the specific “OU” users are in, to remove those cases.
Active Directory Users
Active Directory users will only show in the LDAP Users tab after they have logged in for the first time.
Unlike Local Users, if you wish to make changes to LDAP User’s privileges you must do this from the LDAP Groups panel.

